Mobile Proxy and Their Impact on Secure and Scalable Internet Access
The use of mobile proxies has become essential in today's digital age, as websites closely track user behaviors and the authenticity of their IP. The mobile proxy operates by routing web traffic via authentic mobile devices that are connected to cellular networks, assigning IP addresses to mobile service providers. These IPs are deemed to be extremely secure because they are shared with thousands of legitimate users and frequently change to accommodate normal operating procedures of the mobile network. Unlike data center proxies, which are often flagged or blocked, mobile proxy servers closely resemble everyday smartphone usage. They are particularly efficient for activities that require the use of a normal browsing pattern and constant access to web sites. Businesses, marketers, developers, and researchers increasingly rely on mobile proxies in order to work efficiently in online environments that are restricted. While websites improve their security mechanisms, the importance of authentic IP authentication via mobile devices is growing. 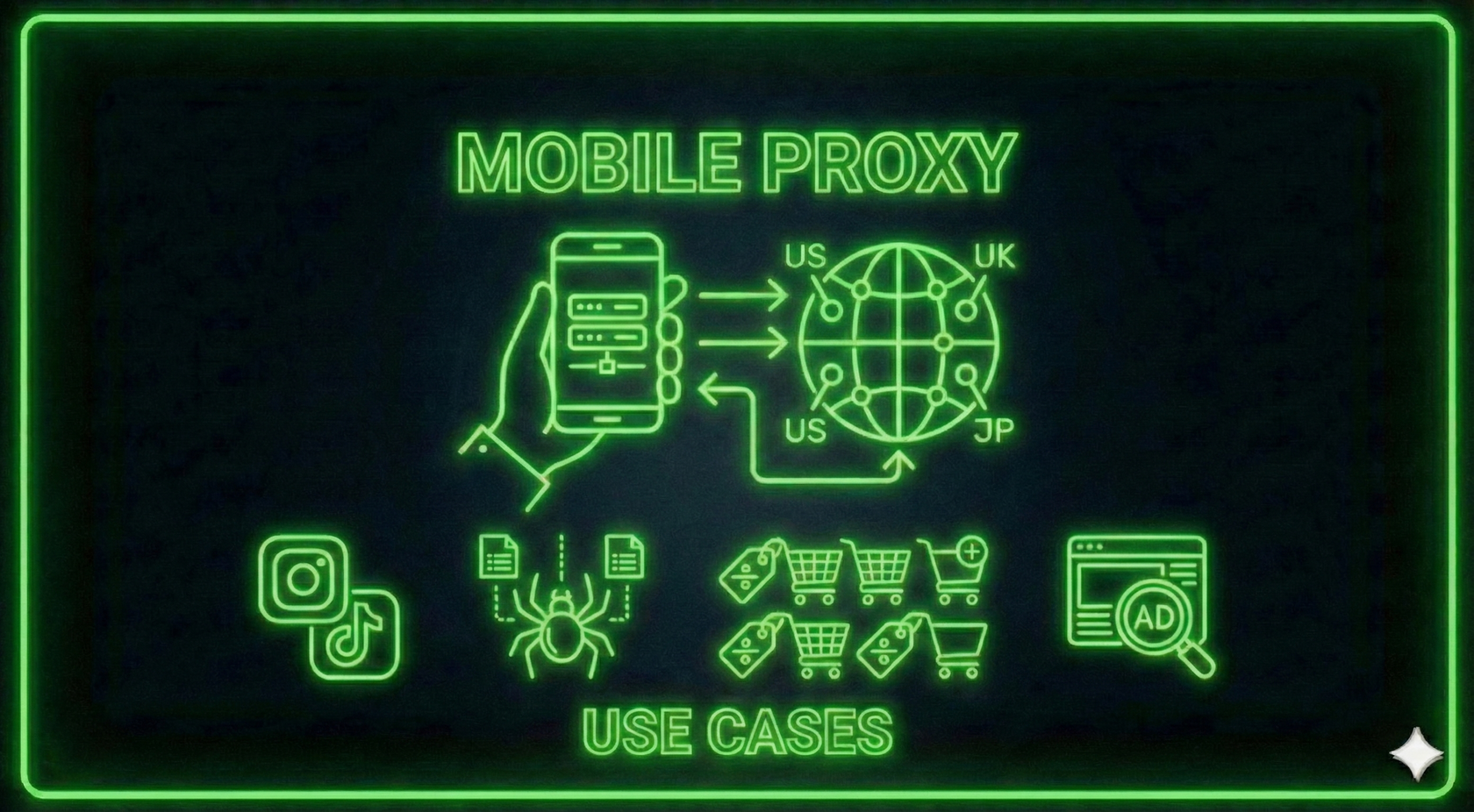 On a technical level mobile proxy services work by directing requests to authentic smartphones, tablets or mobile modems that are connected to 4G, 3G or 5G networks. Each request made through an mobile proxy seems to originate from a genuine mobile device, with carrier-grade network characteristics. This makes detection very difficult for sites that attempt to limit automatized behavior or enforce strict access control. Mobile IP addresses are often changing, which means they change frequently as devices reconnect to the network or move between towers. The natural rotation of IP addresses helps users to avoid IP bans and rate limits as is the case with static IP addresses. Mobile proxies' infrastructure is more complex and costly in comparison to other types of proxy and that is the reason they tend to be priced more expensive. However, the technical advantages that they offer often justifies the expense in critical usage cases. A further characteristic of mobile proxy servers is their constant IP rotation. This enhances privacy and lowers the possibility of being banned. Mobile network operators often assign IP addresses to mobile devices frequently, often every few minutes or for hours. This automatic rotation allows users of mobile proxies to be seen as completely new visitors with each session or demand. If you are working on massive data collection, or managing accounts, this feature is particularly useful. It reduces the risk of triggering rate limits capstchas, rate limits, or other permanently blocked websites. Additionally, mobile proxies can be programmed to switch IPs in accordance with time periods or certain actions, providing the flexibility to meet different needs. The flexibility of mobile proxies makes them ideal for smaller-scale projects as well as enterprises-level initiatives. This results in a more smooth flow of work, which is more effective and with fewer interruptions. A further advantage of Mobile Proxies is its function in the field of social media and the management of accounts. Social media sites are extremely vigilant in identifying unusual activities, multiple logins, or automated behavior using the same IP. Mobile proxy services help reduce this risk by assigning IPs that are comparable to the ones used by the majority of smartphone users. This is perfect to manage several accounts, running promotions, or carrying out influencer outreach without regular account suspensions. Because mobile IPs are shared, IPs further enhances trust, because platforms will not restrict an IP that is that is used by a large number of genuine users. for agencies and companies that means better operation and reduced downtime. As social media continues to play a major role in marketing channel and mobile proxies provide strategic advantage.
On a technical level mobile proxy services work by directing requests to authentic smartphones, tablets or mobile modems that are connected to 4G, 3G or 5G networks. Each request made through an mobile proxy seems to originate from a genuine mobile device, with carrier-grade network characteristics. This makes detection very difficult for sites that attempt to limit automatized behavior or enforce strict access control. Mobile IP addresses are often changing, which means they change frequently as devices reconnect to the network or move between towers. The natural rotation of IP addresses helps users to avoid IP bans and rate limits as is the case with static IP addresses. Mobile proxies' infrastructure is more complex and costly in comparison to other types of proxy and that is the reason they tend to be priced more expensive. However, the technical advantages that they offer often justifies the expense in critical usage cases. A further characteristic of mobile proxy servers is their constant IP rotation. This enhances privacy and lowers the possibility of being banned. Mobile network operators often assign IP addresses to mobile devices frequently, often every few minutes or for hours. This automatic rotation allows users of mobile proxies to be seen as completely new visitors with each session or demand. If you are working on massive data collection, or managing accounts, this feature is particularly useful. It reduces the risk of triggering rate limits capstchas, rate limits, or other permanently blocked websites. Additionally, mobile proxies can be programmed to switch IPs in accordance with time periods or certain actions, providing the flexibility to meet different needs. The flexibility of mobile proxies makes them ideal for smaller-scale projects as well as enterprises-level initiatives. This results in a more smooth flow of work, which is more effective and with fewer interruptions. A further advantage of Mobile Proxies is its function in the field of social media and the management of accounts. Social media sites are extremely vigilant in identifying unusual activities, multiple logins, or automated behavior using the same IP. Mobile proxy services help reduce this risk by assigning IPs that are comparable to the ones used by the majority of smartphone users. This is perfect to manage several accounts, running promotions, or carrying out influencer outreach without regular account suspensions. Because mobile IPs are shared, IPs further enhances trust, because platforms will not restrict an IP that is that is used by a large number of genuine users. for agencies and companies that means better operation and reduced downtime. As social media continues to play a major role in marketing channel and mobile proxies provide strategic advantage.  However, despite their numerous advantages mobile proxies have some problems that users need to consider. Mobile proxies' cost is significantly higher compared to residential or data center proxies, which may limit accessibility for smaller users. The speed of network connections and their stability vary depending on carrier performance as well as the coverage of geographic. Since mobile proxies rely on cellular networks, they could encounter occasional delays or connection drops. Ethics and legal considerations are crucial, since misuse of the platform could be in violation of policies or local law. Users must ensure that their actions are in line with the acceptable usage standards. Becoming aware of the limitations can help organizations use mobile proxy servers efficiently and responsibly. In the near future, the development of mobile proxy servers is dependent on the development of mobile networks and online security technologies. The rollout globally of 5G technology is anticipated to improve the performance of mobile proxy services through faster speeds and less latency. At the same time sites and platforms are expected to be able to improve their detection methods, further increasing the demand for high-quality, authentic IP sources. Proxies for mobile devices are likely to remain a premium solution for users who require the highest level of trust and realism when they engage in internet-based interactions. As online ecosystems grow increasingly complex it is likely that the compromise between privacy, access, and security will grow more important. Mobile proxy servers are situated in the middle of these issues, and offer an effective solution to navigate today's internet-related challenges. Their continual adoption is a reflection of the ongoing need for devices that are closely aligned with the real-time online behaviour of humans.
However, despite their numerous advantages mobile proxies have some problems that users need to consider. Mobile proxies' cost is significantly higher compared to residential or data center proxies, which may limit accessibility for smaller users. The speed of network connections and their stability vary depending on carrier performance as well as the coverage of geographic. Since mobile proxies rely on cellular networks, they could encounter occasional delays or connection drops. Ethics and legal considerations are crucial, since misuse of the platform could be in violation of policies or local law. Users must ensure that their actions are in line with the acceptable usage standards. Becoming aware of the limitations can help organizations use mobile proxy servers efficiently and responsibly. In the near future, the development of mobile proxy servers is dependent on the development of mobile networks and online security technologies. The rollout globally of 5G technology is anticipated to improve the performance of mobile proxy services through faster speeds and less latency. At the same time sites and platforms are expected to be able to improve their detection methods, further increasing the demand for high-quality, authentic IP sources. Proxies for mobile devices are likely to remain a premium solution for users who require the highest level of trust and realism when they engage in internet-based interactions. As online ecosystems grow increasingly complex it is likely that the compromise between privacy, access, and security will grow more important. Mobile proxy servers are situated in the middle of these issues, and offer an effective solution to navigate today's internet-related challenges. Their continual adoption is a reflection of the ongoing need for devices that are closely aligned with the real-time online behaviour of humans.